Patch #29606
closedSupport self-signed LDAPS connections
Description
With the introduction of certficate checks to LDAPS connections in trunk #24970 (and maybe 3.4 in #29476), we should enable the user to fall back to the old behavior, where server certificates were not checked.
This is especially important, where local domain controllers and LDAP servers are used as an authentication backend. Because there servers will often use self-signed certificates.
The attached patch adds a configuration option to disable the certificate checks for LDAPS connections.
Implementation¶
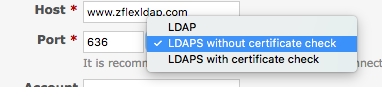
The patch adds a new boolean column to auth_sources called verify_peer. The LDAP auth source edit screen is extended so that users may decide if they want to use "LDAP", "LDAPS without certificate check" (this one is new) or "LDAPS with certificate check".
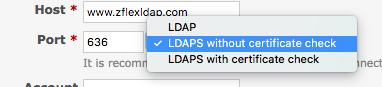
Depending on the selected option, the tls and verify_peer attributes are set on the auth source.
Furthermore the patch extends the LDAP connection setup code, to use the newly introduced setting.
Backwards compatibility¶
To ensure backwards compatibility with the current Redmine trunk, the new column verify_peer defaults to true. This way, connections which use tls will continue checking the certificates.
If you want to stay compatible with the behavior in the latest Redmine release, then the default value should be false, since 3.4 currently doesn't verify certificates, as explained in #29476.
I chose to introduce a new column instead of changing the existing one, so that the db schema remains compatible with other auth sources, which may be used by plugins. Adding a new column, should not break any existing code.
Redmine.pm compatibility¶
Redmine.pm currently does not verify certificates.
A brief check suggests, that the library which is used in Redmine.pm simpy doesn't support checking server certificates. Therefore in order to properly secure LDAP authentication for SVN and/or to support this new configuration, Redmine.pm would need to switch to a different LDAP library. But this would be out of scope for this ticket. This patch neither improves nor worsens the security of Redmine.pm's LDAP authentication.
Related issues¶
- #24970 introduces server certificate checks for LDAPS for Redmine 4.0
- #29476 suggests to backport #24970 to Redmine 3.4
- #27071 seems to be facing the problem, that the certficate cannot be validated
- #3358 was suggesting (among others) a similar feature
The attached patch is targeted at r17480.
Files
Related issues
 Updated by Holger Just over 7 years ago
Updated by Holger Just over 7 years ago
- Related to Defect #24970: Net::LDAP::LdapError is deprecated added
 Updated by Holger Just over 7 years ago
Updated by Holger Just over 7 years ago
- Related to Defect #29476: Update net-ldap to 0.16.0 added
 Updated by Holger Just over 7 years ago
Updated by Holger Just over 7 years ago
- Related to Defect #27071: Error testing LDAPS Connection: "Unable to connect (hostname X.X.X.X does not match the server certificate)" added
 Updated by Holger Just over 7 years ago
Updated by Holger Just over 7 years ago
- Related to Patch #3358: Advanced LDAP authentication added
 Updated by Go MAEDA over 7 years ago
Updated by Go MAEDA over 7 years ago
- Category set to Accounts / authentication
- Target version set to 4.0.0
Using self-signed certificates is not so uncommon for on-premises. Setting the target version to 4.0.0.
 Updated by Gregor Schmidt over 7 years ago
Updated by Gregor Schmidt over 7 years ago
- File 0001-Allow-unchecked-LDAPS-TLS-connections.patch 0001-Allow-unchecked-LDAPS-TLS-connections.patch added
After some internal discussion at Planio, we've decided to further clarify the wording. Attached you may find an updated patch. It only differs in the locale files.
It should be now more clear, that LDAPS with certificate check should be considered proper LDAPS, while the option without certificate check is merely an exception for special use cases.
I've also replaced authorization with authentication in the new texts.
 Updated by Go MAEDA over 7 years ago
Updated by Go MAEDA over 7 years ago
- Related to Defect #8068: LDAP Authentificaton doesn't verify certificate validity added
 Updated by Go MAEDA over 7 years ago
Updated by Go MAEDA over 7 years ago
- Category changed from Accounts / authentication to LDAP