Defect #4483
open
LDAP authentication with Redmine doesn't return an error when credentials used to bind to LDAP are incorrect
Added by Joe Heck about 16 years ago.
Updated about 5 years ago.
Description
When incorrect credentials are used in LDAP authentication with Redmine, the search mechanism will always silently fail because the code in 0.8.7 doesn't check for bind success before searching.
I'm using ruby 1.8.5, rails 2.1.2, passenger 2.2.8, redmine 0.8.7, MySQL 5, on RHEL5.
I added the debugging line:
logger.debug "Connection #{ldap_con} bind result was #{ldap_con.bind}" if logger && logger.debug?
to the code at /app/models/auth_source_ldap.rb to identify that the error occuring was incorrect credentials. However, silent failure seems to be a bug, especially since the "test" link on the auth_sources page appeared to work correctly.
Files
I've just ran over the very same problem. I suggest change code of AuthSourceLdap.test_connection to something like this:
def test_connection
ldap_con = initialize_ldap_con(self.account, self.account_password)
if not ldap_con.bind
raise "Failed to bind to LDAP server."
rescue Net::LDAP::LdapError => text
raise "LdapError: " + text
end
This will make Test button to show error when you provide bad bind credentials, not just write success.
I confirm, Redmine version 2.5.2.
Only after research in WireShark I saw the error:
LDAPMessage bindResponse(1) invalidCredentials (80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 531, vece)
which means "not permitted to logon at this workstation".
Redmine always reports "Success".
Joe Heck wrote:
However, silent failure seems to be a bug, especially since the "test" link on the auth_sources page appeared to work correctly.
I think the reason the test connection was successful is that you didn't enter your account or password.
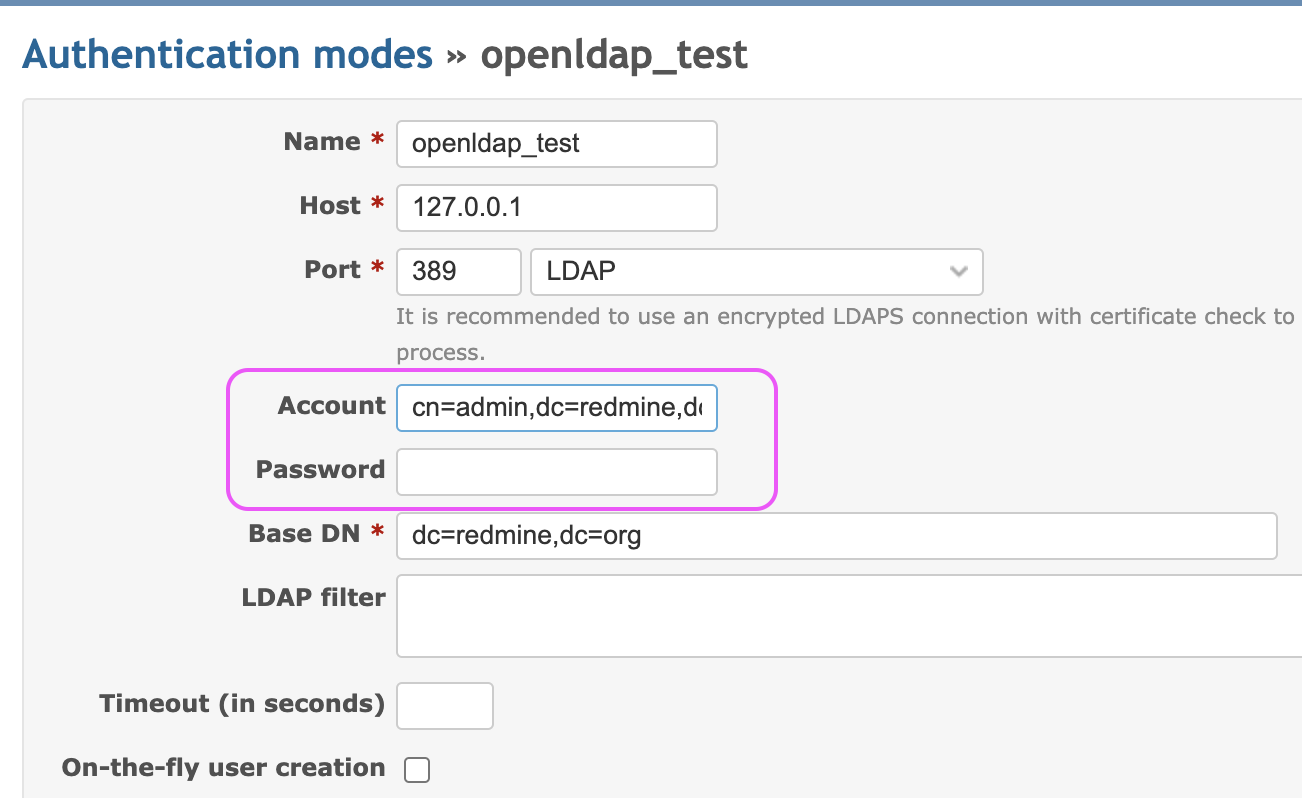
Alternatively, the test connection will succeed even when the Dynamic Bind Account is set for the account.
RedmineLDAP
I think the following patch will solve it.
diff --git a/app/models/auth_source_ldap.rb b/app/models/auth_source_ldap.rb
index 7adbf45bc..3642b3b31 100644
--- a/app/models/auth_source_ldap.rb
+++ b/app/models/auth_source_ldap.rb
@@ -71,10 +71,9 @@ class AuthSourceLdap < AuthSource
with_timeout do
ldap_con = initialize_ldap_con(self.account, self.account_password)
ldap_con.open {}
- if self.account.present? && !self.account.include?("$login") && self.account_password.present?
- ldap_auth = authenticate_dn(self.account, self.account_password)
- raise AuthSourceException.new(l(:error_ldap_bind_credentials)) if !ldap_auth
- end
+ return if self.account.present? && self.account.include?("$login")
+ ldap_auth = authenticate_dn(self.account, self.account_password)
+ raise AuthSourceException.new(l(:error_ldap_bind_credentials)) if !ldap_auth
end
rescue *NETWORK_EXCEPTIONS => e
raise AuthSourceException.new(e.message)
Also available in: Atom
PDF
