Defect #33846
closedInline issue auto complete doesn't sanitize HTML tags
Added by Fernando Hartmann over 4 years ago. Updated about 4 years ago.
0%
Description
If referring a issue that have a HTML tag in subject, the tag is rendered as an object in the auto complete tip.
To reproduce- Create one issue with a subject like
Test <select> tag - Start a new issue, go to description field and type issue number created above
- We should display something like
Feature #xxxx Test <select> tag - We display a
selectobject rendered in the tip, like image bellow
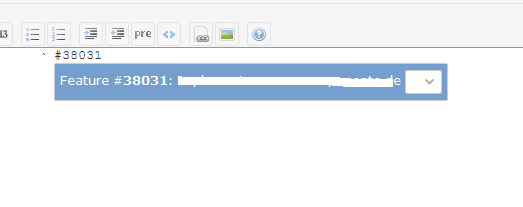
This can be dangerous,as some one can inject HTML
Files
| tip.png (6.45 KB) tip.png | Fernando Hartmann, 2020-08-12 19:26 | ||
| sanitize_html.patch (868 Bytes) sanitize_html.patch | Marius BĂLTEANU, 2020-10-05 22:51 | ||
| autocomplete-by-title.png (56.7 KB) autocomplete-by-title.png | Go MAEDA, 2020-10-15 14:01 | ||
| sanitize_html_v2.patch (1.01 KB) sanitize_html_v2.patch | Marius BĂLTEANU, 2020-10-16 07:47 | ||
| tribute.png (132 KB) tribute.png | Marius BĂLTEANU, 2020-10-16 07:49 | ||
| sanitize_html_v3.patch (878 Bytes) sanitize_html_v3.patch | Marius BĂLTEANU, 2020-10-16 08:01 | ||
| test_for_33846.patch (809 Bytes) test_for_33846.patch | Marius BĂLTEANU, 2020-12-05 18:10 | ||
| sanitize_html_v4.patch (2.18 KB) sanitize_html_v4.patch | Go MAEDA, 2021-03-15 16:52 |
Related issues
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- Related to Feature #31989: Inline issue auto complete (#) in fields with text-formatting enabled added
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File sanitize_html.patch sanitize_html.patch added
- Target version set to 4.1.2
Fernando, thanks for catching this.
I've attached a patch to fix this issue.
 Updated by Go MAEDA over 4 years ago
Updated by Go MAEDA over 4 years ago
Marius BALTEANU wrote:
I've attached a patch to fix this issue.
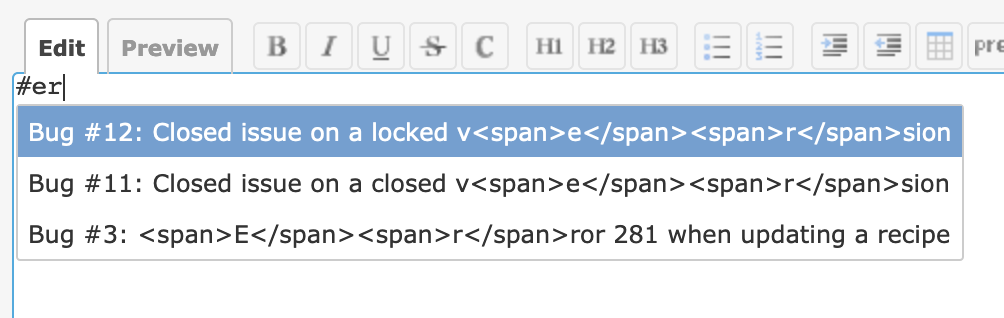
Thank you for fixing the issue but I see <span> tags when using auto-complete by issue subject.
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- Assignee set to Marius BĂLTEANU
Thanks for pointing this out, I was able to reproduce the problem. I will post soon a fix.
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File sanitize_html_v2.patch sanitize_html_v2.patch added
- File tribute.png tribute.png added
- Assignee deleted (
Marius BĂLTEANU)
Please try this new version, it should work as expected with one mention: the letters that match the search are no longer highlighted.

Also, instead of the sanitzeHTML function, I think it's better to use a library like https://lodash.com/docs/4.17.15#escape, but I'm not sure how to add it without copying the code or by using a module bundler like webpack. @Jean-Philippe, any recommendations on this?
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File sanitize_html_v3.patch sanitize_html_v3.patch added
This one works on IE 11 as well.
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
Attached is a test for this issue that can be applied only after #34123 is committed.
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File test_for_26089.patch.zip added
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File deleted (
test_for_26089.patch.zip)
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- File test_for_33846.patch test_for_33846.patch added
 Updated by Marius BĂLTEANU about 4 years ago
Updated by Marius BĂLTEANU about 4 years ago
- Assignee changed from Jean-Philippe Lang to Go MAEDA
 Updated by Go MAEDA about 4 years ago
Updated by Go MAEDA about 4 years ago
- File sanitize_html_v4.patch sanitize_html_v4.patch added
Update the patch for the latest trunk (r20791).
 Updated by Go MAEDA about 4 years ago
Updated by Go MAEDA about 4 years ago
- Status changed from New to Closed
- Resolution set to Fixed
Committed the fix. Thank you all for your contribution.
 Updated by Go MAEDA about 4 years ago
Updated by Go MAEDA about 4 years ago
- Subject changed from Inline issue auto complete (#) doesn't sanityze HTML tags to Inline issue auto complete doesn't sanitize HTML tags
 Updated by Holger Just about 4 years ago
Updated by Holger Just about 4 years ago
By the way: this a full-blown XSS vulnerability. With an issue subject such as
<span onmouseover="alert('pwned');">This is some exciting text</span>
arbitrary Javascript can be executed (as well as arbitrary HTML code shown). In my opinion, the assessment of the issue in Security_Advisories should therefore be increased to High.
 Updated by Marius BĂLTEANU about 4 years ago
Updated by Marius BĂLTEANU about 4 years ago
Holger Just wrote:
By the way: this a full-blown XSS vulnerability. With an issue subject such as
[...]
arbitrary Javascript can be executed (as well as arbitrary HTML code shown). In my opinion, the assessment of the issue in Security_Advisories should therefore be increased to High.
Thanks Holger, I've changed to High.