Feature #24808
closedOAuth2 support for Redmine API Apps (OAuth2 Provider)
Description
I think, we should make Redmine an OAuth2 provider, so that client apps using Redmine's API can ask users to authenticate rather than asking for an API key. Another goal would be to limit access to API client apps, so that not all apps gain access to the full scope of data a user has access to.
I'm working on this currently and I will hopefully be able to submit a patch soon. Here's a first screenshot:
Files
Related issues
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- File authorized_apps.png authorized_apps.png added
- File my_account.png my_account.png added
- File auth_prompt.png auth_prompt.png added
- File apps.png apps.png added
- File 0001-Use-named-routes-for-search-in-base-layout.patch 0001-Use-named-routes-for-search-in-base-layout.patch added
- File 0002-Prevent-hash-type-URLs-from-being-namespaced-in-Menu.patch 0002-Prevent-hash-type-URLs-from-being-namespaced-in-Menu.patch added
- File 0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch added
- File 0004-Redmine-style-UI-for-Doorkeeper-OAuth2-provider.patch 0004-Redmine-style-UI-for-Doorkeeper-OAuth2-provider.patch added
- File 0005-Add-optional-scope-parameter-to-Role-allowed_to.patch 0005-Add-optional-scope-parameter-to-Role-allowed_to.patch added
- File 0006-Use-Redmine-s-permissions-as-OAuth2-scopes.patch 0006-Use-Redmine-s-permissions-as-OAuth2-scopes.patch added
- Status changed from New to Needs feedback
- Assignee deleted (
Jan from Planio www.plan.io)
The attached patch series implements full OAuth2 provider support for Redmine.
Background¶
OAuth2 is a widely adopted protocol for granting access to API client applications. More information can be found here:
Screenshots¶
Here are a few screenshots that show how it looks like:
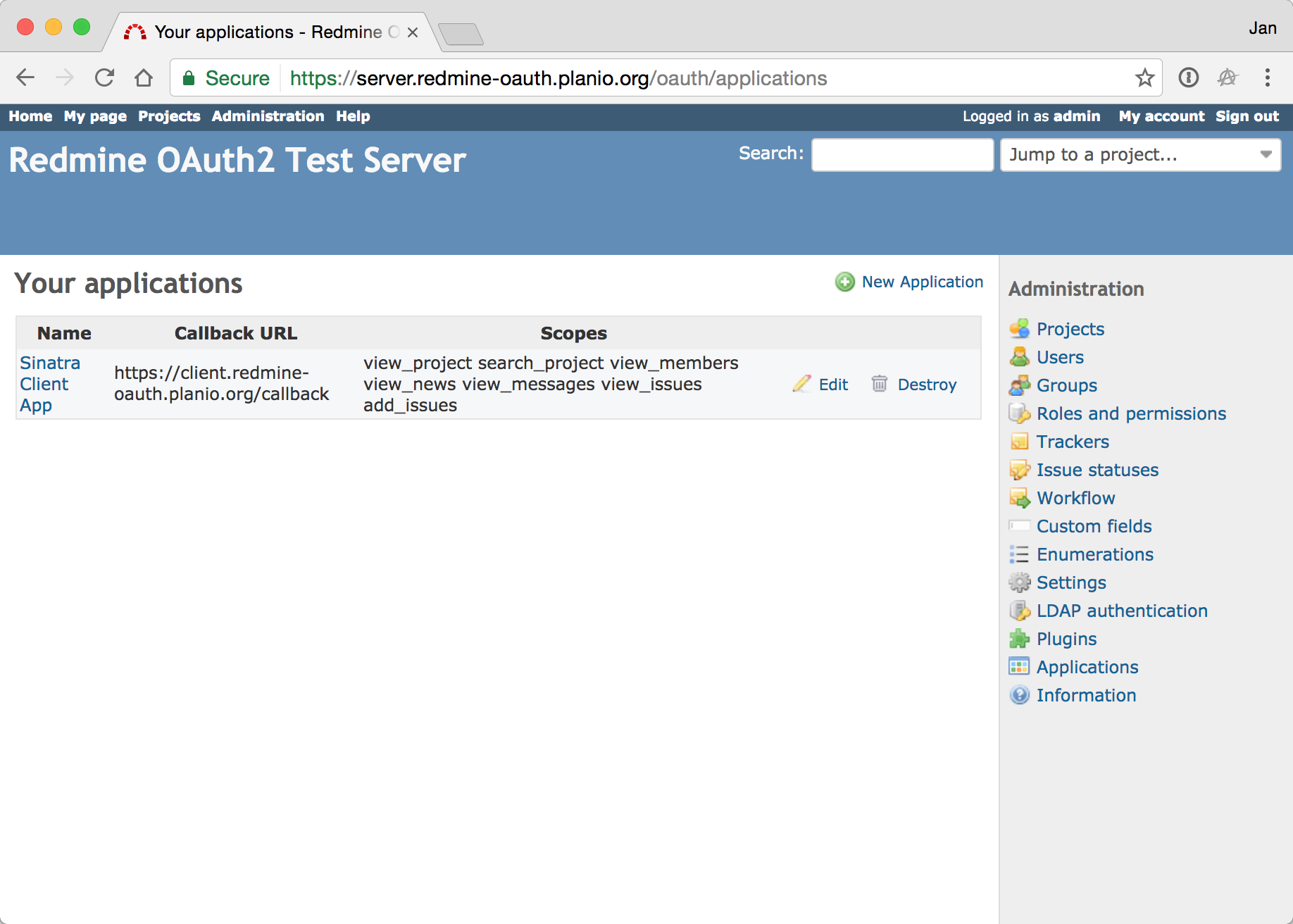
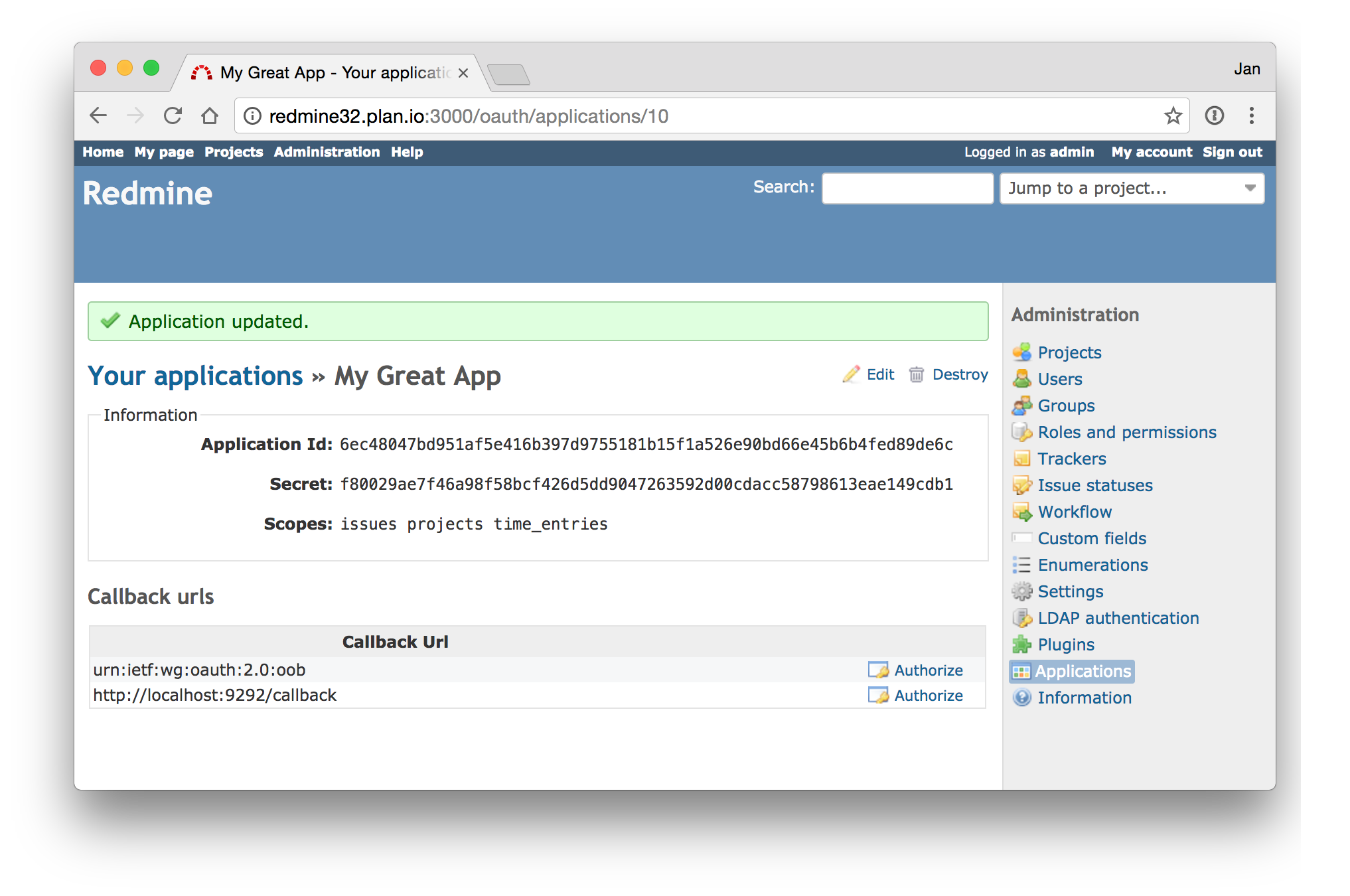
Admins are able to create/modify/delete OAuth2 client apps from the user interface.

OAuth2 App credentials are generated and can then be used in API clients.

In order for an App to gain access to Redmine, it must ask the user for permission.
Regular users are able to see which apps currently have access to their data from their My Account area.
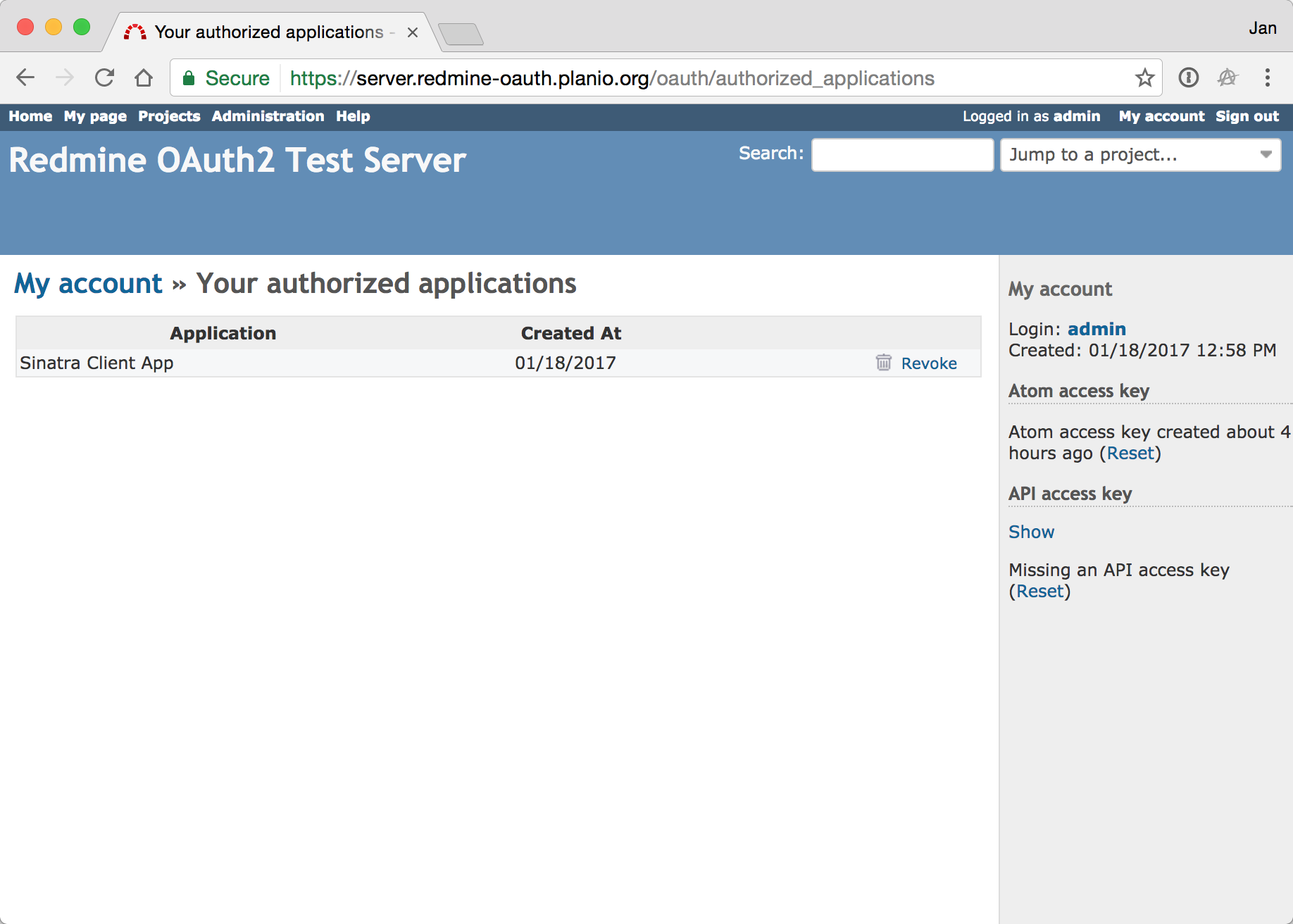
Regular users are able to revoke access to individual apps.
Live Demo¶
We are providing a live demo server and client via these links:
https://server.redmine-oauth.planio.org¶
Username/Password is admin:oauth2. The content on this server will be reset every 60 minutes. Feel free to create your own OAuth2 applications via the Admin section, but please don't modify/delete the "Sinatra Client App".
https://client.redmine-oauth.planio.org¶
You can use this app to try out the authentication/authorization flow. Feel free to create your own user accounts on the Redmine server for this.
The /issues API will only work if the view_issues scope is requested. If only the standard scopes are requested, you will see an error here (on purpose).
Feel free to download the client app code from our Planio repository to try out everything locally.
The patch series¶
0001changes the base layout to use named routes. The old hash-style routes (e.g.{controller => 'search', :action => 'index'}) would get namespaced when the layout is used in a namespaced controller in a plugin or engine which is the case with the Doorkeeper gem introduced later.0002changes the MenuManager in a similar way and prevents the rendered menu links from getting namespaced in the above scenario.0003adds the Doorkeeper Gem and integrates it with Redmine in the relevant places. You could apply patches0001-0003only to get functioning OAuth2 provider support already. In detail, what happens is:Gemfile- Gem is added inapp/controllers/application_controller.rb- Doorkeeper is used as a new optional authentication mechanism that is tried when regular Redmine API auth failsapp/views/my/account.html.erb- Link to Doorkeeper's views for managing a user's authorized appsconfig/initializers/doorkeeper.rb- Configure Doorkeeper so that it ties in with Redmine's user and admin authenticationconfig/routes.rb- Add Doorkeeper specific routes androot_urlwhich is needed by itdb/migrate/20170107092155_create_doorkeeper_tables.rb- Migrations to add Doorkeeper tableslib/redmine.rb- Link to Doorkeeper's views for managing available apps within the admin sectionpublic/stylesheets/application.css- Icon for Appstest/unit/lib/redmine/i18n_test.rb- Fix locale counting in tests because doorkeeper-i18n introduces languages unknown to Redmine
0004- integrates Doorkeeper further by overriding all views with Redmine compatible markup and makes use of Redmine'sdeny_accessandrequire_loginmethods which become available once the Doorkeeper controllers are set to inherit from Redmine'sApplicationController0005- changesRole#allowed_to?so that it can accept an optionalscopeparameter which can be an array of permission symbols that will be used as a logicalANDfilter.0006- Allows OAuth2 client apps to use Redmine permissions as Scopes in the sense of OAuth2. This way, admins and application developers can limit the abilities of client apps. An app will generally have at most the permissions defined by the App definition or as reqested by the app during the auhtorization step. Of course, the app will never have more permissions than the user is has requested authorization for would have in a normal interactive scenario.
Considerations¶
Why use Doorkeeper?¶
Implementing OAuth2 "by hand" seemed like re-inventing the wheel. Building and maintaining such security-critical code is both error-prone and non-trivial. The Doorkeeper Gem is the de-facto standard solution for implementing an OAuth2 provider in Rails. It's tried and tested, well-maintained and used by many high profile apps and services.
Integrating it with Redmine required only minor changes to Redmine's code base itself which should hopefully make maintenance of this functionality quite easy.
Why can only admins create apps?¶
The decision that only Redmine admins can add new API client applications is debatable, but it felt like the easiest solution for this first version. Allowing regular users to create apps would have required more overridden Doorkeeper controllers, new Redmine permissions (e.g. add_apps, view_apps, destroy_apps, etc.)
In addition to that, enabling/diasbling things like the REST API, JSONP support, etc. is currently also only available to admins, so I thought it would be consistent.
Some translations are missing! Where are the I18n keys?¶
At the moment, I've included them via the doorkeeper-i18n Gem. Technically, we could pull the locales in to Redmine's code base. However, – in the spirit of open source – I'd advcate in favor of keeping them in the external Gem and working with the Doorkeeper maintainers to improve them if needed. I've fixed two issues with the locales already via pull requests and they were accepted rather quickly.
That's it for now. I am looking forward to your feedback!
 Updated by Marius BĂLTEANU about 9 years ago
Updated by Marius BĂLTEANU about 9 years ago
IMO, I think that the OAuth2.0 provider will be a great addition to Redmine and a feature that we'll use for sure at our future integrations with other apps.
What I like very much is the separation between the users and applications. Now we've some users named like "<application_name>-Generic User" used to authenticate the API calls. Having the possibility to define them as apps and manage their permissions from a different screen is very useful.
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- Description updated (diff)
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- File deleted (
0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch)
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- File 0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch added
Slightly updated version of 0003, using wider columns for scopes
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- File deleted (
0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch)
 Updated by Jan from Planio www.plan.io about 9 years ago
Updated by Jan from Planio www.plan.io about 9 years ago
- File 0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch 0003-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch added
And another fix.
 Updated by Cheyenne Wills over 8 years ago
Updated by Cheyenne Wills over 8 years ago
+1
What is the current "status" of this? Is this kind of planned for a future release?
We have two apps that could benefit by this (I've been looking at the redmine_oauth_provider plugin, but it appears that it doesn't work with the current level of Redmine).
 Updated by Peter Volkov over 6 years ago
Updated by Peter Volkov over 6 years ago
I think that "Needs feedback" is a wrong status here. According to #12827 this status means that this ticket is waiting for author's feedback, and such tickets are invisible for developers. Jan could you updated patchset and Status here?
 Updated by Jan from Planio www.plan.io over 6 years ago
Updated by Jan from Planio www.plan.io over 6 years ago
- Status changed from Needs feedback to New
I'm setting the status to New then, as requested. Ideally, we could get some more feedback from other contributors if the feature is desired and if yes, I'd be happy to rebase the patches on current trunk.
 Updated by Bernhard Rohloff over 6 years ago
Updated by Bernhard Rohloff over 6 years ago
I think it can be a nice feature for Redmine and would make it much easier to manage things like bots, dashboards and applications of that kind. IMHO it's definitely worth a rebase.
+1
 Updated by Jens Krämer over 5 years ago
Updated by Jens Krämer over 5 years ago
- File 0001-oauth-Use-named-routes-in-base-layout-and-account-si.patch 0001-oauth-Use-named-routes-in-base-layout-and-account-si.patch added
- File 0002-oauth-Prevent-hash-type-URLs-from-being-namespaced-i.patch 0002-oauth-Prevent-hash-type-URLs-from-being-namespaced-i.patch added
- File 0003-oauth-Add-OAuth2-provider-capability-using-doorkeepe.patch 0003-oauth-Add-OAuth2-provider-capability-using-doorkeepe.patch added
- File 0004-oauth-Redmine-style-UI-for-Doorkeeper-OAuth2-provide.patch 0004-oauth-Redmine-style-UI-for-Doorkeeper-OAuth2-provide.patch added
- File 0005-oauth-Add-optional-scope-parameter-to-Role-allowed_t.patch 0005-oauth-Add-optional-scope-parameter-to-Role-allowed_t.patch added
- File 0006-oauth-Use-Redmine-s-permissions-as-OAuth2-scopes.patch 0006-oauth-Use-Redmine-s-permissions-as-OAuth2-scopes.patch added
- File 0007-oauth-adds-system-test-to-test-the-oauth-provider-ca.patch 0007-oauth-adds-system-test-to-test-the-oauth-provider-ca.patch added
I rebased this patch on current master and added a brief system test that covers application creation, authorization and usage with an actual oauth2 client.
I'd also like to add that, since a few weeks, we're using this feature successfully at Planio for authenticating the native Planio Storage client apps.
 Updated by Jan from Planio www.plan.io over 5 years ago
Updated by Jan from Planio www.plan.io over 5 years ago
- Target version set to Candidate for next minor release
Thanks Jens. I would really enjoy seeing this making its way into a future Redmine release and I believe it will help Redmine get more third party apps and integrations!
 Updated by Jens Krämer over 5 years ago
Updated by Jens Krämer over 5 years ago
- File 0001-Use-named-routes-in-base-layout-and-account-sidebar.patch 0001-Use-named-routes-in-base-layout-and-account-sidebar.patch added
- File 0002-Prevent-hash-type-URLs-from-being-namespaced-in-Menu.patch 0002-Prevent-hash-type-URLs-from-being-namespaced-in-Menu.patch added
- File 0003-Add-optional-scope-parameter-to-Role-allowed_to.patch 0003-Add-optional-scope-parameter-to-Role-allowed_to.patch added
- File 0004-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch 0004-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch added
Another update to this patch. Notable changes are:
- updated to Doorkeeper 5.4, which allowed for the following improvements:
- secrets (tokens, application secret) are now stored as hashes
- support for PKCE (most relevant for non-confidential clients)
- introduced an
adminscope which allows Administrators to grant admin permissions to client applications - fixed a stored CSRF vulnerability that was present in one of the original Doorkeeper templates. It was only exploitable by Administrators but if you're using an older version of this patch, at least update your views according to this doorkeeper commit
We also just released the omniauth-redmine-oauth2 gem (source code at Planio and Github). We also built a small Rails app to demonstrate usage of the gem .
Currently this patch makes two I18n tests fail. This is due to the inclusion of the doorkeeper-i18n gem, which introduces 4 locales that aren't present in Redmine. In general, we would need to decide if we want to include these 3rd party translation at all (they do not cover all of Redmine's locales by a large margin) or if we incorporate them into Redmine. As of now the patch just overrides a few strings to make the wording more Redmine-like.
Due to the Doorkeeper upgrade I was more or less forced to squash the last 4 commits of the previous patch series, so it's down to 4 commits now.
 Updated by Marius BĂLTEANU almost 5 years ago
Updated by Marius BĂLTEANU almost 5 years ago
- Target version changed from Candidate for next minor release to Candidate for next major release
Jens, I've started to look to the provided patches and to test this feature. For now, I've committed all 4 patches to the Gitlab instance in order to get the tests results. Besides the I18n test fails, there are some Rubocop warnings that should be fixed.
Am I wrong if I say that patches 0001 and 0002 can be extracted from this issue and delivered as separated ticket? In this way, we will down this feature to 2 patches and it will be easier to maintain/rebase it.
I've assigning this to the next major release version because the changes are too huge for a minor version.
 Updated by Jens Krämer almost 5 years ago
Updated by Jens Krämer almost 5 years ago
 Updated by Jan from Planio www.plan.io almost 5 years ago
Updated by Jan from Planio www.plan.io almost 5 years ago
Thanks Marius for looking into this. I think it should greatly improve the Redmine API to use state of the art authorization!
 Updated by Jens Krämer almost 5 years ago
Updated by Jens Krämer almost 5 years ago
- File 0003-Add-optional-scope-parameter-to-Role-allowed_to.patch 0003-Add-optional-scope-parameter-to-Role-allowed_to.patch added
- File 0004-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch 0004-Add-OAuth2-provider-capability-using-doorkeeper-gem.patch added
here are the remaining two patches, updated to the most recent doorkeeper release (5.5.1), rebased on current master, and hopefully with a lot less rubocop warnings.
 Updated by Marius BĂLTEANU over 4 years ago
Updated by Marius BĂLTEANU over 4 years ago
- Assignee set to Marius BĂLTEANU
- Target version changed from Candidate for next major release to 5.0.0
 Updated by Harald Welte almost 4 years ago
Updated by Harald Welte almost 4 years ago
Excellent proposal, looking forward to seeing this merged for the next major release.
 Updated by Marius BĂLTEANU almost 4 years ago
Updated by Marius BĂLTEANU almost 4 years ago
- Target version changed from 5.0.0 to Candidate for next major release
The patches need some changes to work with Rails 6 and zeitwerk autoloader.
 Updated by Gael Duret over 3 years ago
Updated by Gael Duret over 3 years ago
Hello All,
We actually use RedMine in our company and we use the IMAP fetching email process to create our tickets. This process will stop working on October first as we are connected to an Office365 server and Microsoft will deactivate the basic authentication.
We are looking for a way to use OAuth authentication.
Our Redmine version:
Environment:
Redmine version 5.0.0.stable
Ruby version 2.6.9-p207 (2021-11-24) [x64-mingw32]
Rails version 6.1.4.7
Environment production
Database adapter Mysql2
Mailer queue ActiveJob::QueueAdapters::AsyncAdapter
Mailer delivery smtp
We do not have any Rugby knowledge in the team, we are looking for some explain / help on this subject ?
Which patch for our version ? How to setup a patch ?
Thanks
![pasquale [:dedalus]](https://www.gravatar.com/avatar/26f9564a55a0011c2db18d783c85cc08?rating=PG&size=24&default=identicon) Updated by pasquale [:dedalus] about 2 years ago
Updated by pasquale [:dedalus] about 2 years ago
Marius BĂLTEANU Go MAEDA
Could this ticket be included in the activities planned for version 6.0?
 Updated by Marius BĂLTEANU 9 months ago
Updated by Marius BĂLTEANU 9 months ago
- File 0002-Quick-workaround-to-remove-languages-added-by-doorke.patch added
- File 0001-Oauth-provider.patch added
- apply cleanly on the current trunk
- replace the legacy icons with SVG icons
- fix all Rubocop warnings
The tests pass with a quick workaround for the I18n tests.
Before integrating this to the core, we still need to:- Decide what to do with the 4 extra languages added by doorkeeper-i18n gem (
[:be, :nb, :"zh-CN", :"zh-HK"] - Update doorkeeper gem to the latest version
- Replace WEBrick with Puma in the system tests
I will try to handle all these points in the following weeks, but any help is appreciated!
 Updated by Go MAEDA 9 months ago
Updated by Go MAEDA 9 months ago
Marius BĂLTEANU wrote in #note-31:
- Decide what to do with the 4 extra languages added by doorkeeper-i18n gem (
[:be, :nb, :"zh-CN", :"zh-HK"]
I don't think Redmine needs to do anything about 'be' (Belarusian), 'nb' (Norwegian Bokmål), and 'zh-HK' (Chinese - Hong Kong). Adding those languages to Redmine's config/locales would add languages that are not well maintained.
However, since 'zh-CN' (Simplified Chinese) is equivalent to Redmine's 'zh', we should map 'zh-CN' to Redmine's 'zh', or Redmine's 'zh' to 'zh-CN' in some way.
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
- File deleted (
0002-Quick-workaround-to-remove-languages-added-by-doorke.patch)
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
- File deleted (
0001-Oauth-provider.patch)
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
- File 0003-Switch-server-used-in-oauth_provider-test-from-webri.patch 0003-Switch-server-used-in-oauth_provider-test-from-webri.patch added
- File 0002-Quick-workaround-to-remove-languages-added-by-doorke.patch 0002-Quick-workaround-to-remove-languages-added-by-doorke.patch added
- File 0001-Oauth-provider.patch 0001-Oauth-provider.patch added
- Target version changed from Candidate for next major release to 6.1.0
I've updated the patches in order to fix all Rubocop warnings, update doorkeeper gem to the latest version and to replace Webrick with Puma. Everything looks good and we can I added it to the core, except the extra languages.
Go MAEDA wrote in #note-32:
[..]
I don't think Redmine needs to do anything about 'be' (Belarusian), 'nb' (Norwegian Bokmål), and 'zh-HK' (Chinese - Hong Kong). Adding those languages to Redmine's
config/localeswould add languages that are not well maintained.
I agree, but removing as I did in the second patch is not the most elegant solution.
Jens Krämer, Holger Just, do you have any better approach?
 Updated by Jens Krämer 8 months ago
Updated by Jens Krämer 8 months ago
Marius BĂLTEANU wrote in #note-35:
I've updated the patches in order to fix all Rubocop warnings, update doorkeeper gem to the latest version and to replace Webrick with Puma. Everything looks good and we can I added it to the core, except the extra languages.
Awesome :)
Go MAEDA wrote in #note-32:
[..]
I don't think Redmine needs to do anything about 'be' (Belarusian), 'nb' (Norwegian Bokmål), and 'zh-HK' (Chinese - Hong Kong). Adding those languages to Redmine's
config/localeswould add languages that are not well maintained.I agree, but removing as I did in the second patch is not the most elegant solution.
I think it is fine like that, and like it better than not using the gem and somehow pulling in just the doorkeeper translations we do want in some other way.
 Updated by Holger Just 8 months ago
Updated by Holger Just 8 months ago
In #38529, we have added a patch to restrict the available_locales to those where we have a matching named file in config/locales. This was mostly (but not only) added to avoid this specific issue with doorkeeper. If that does not work (anymore), we should update this approach instead.
Just blacklisting some named locales seems like a brittle approach which may break on any minor update of doorkeeper or any other gem when it adds additional locales.
 Updated by Holger Just 8 months ago
Updated by Holger Just 8 months ago
- Related to Patch #38529: Limit available locales to those defined by Redmine itself added
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
Thanks Jens and Holger for your quick responses.
Holger Just wrote in #note-37:
In #38529, we have added a patch to restrict the
available_localesto those where we have a matching named file inconfig/locales. This was mostly (but not only) added to avoid this specific issue with doorkeeper. If that does not work (anymore), we should update this approach instead.
Thanks for pointing this out, I was not aware about this change, but for some reason, the change is not working anymore. I've created #42815 to address the problem.
Just blacklisting some named locales seems like a brittle approach which may break on any minor update of doorkeeper or any other gem when it adds additional locales.
I agree.
Once we fix the problem with the locales, I will commit this change.
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
- Status changed from New to Resolved
- Resolution set to Fixed
Now that the issue with locales added by 3rd parties is now fixed, I've finally commit this feature to the core. I will generate the locales and I will replace the webrick with puma in the following days.
Special thanks to Jens and Holger from Plan.io for providing this nice feature!
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
- Status changed from Resolved to Closed
- the system test passes now on Github CI
- webrick was replaced by puma
 Updated by Takenori TAKAKI 8 months ago
Updated by Takenori TAKAKI 8 months ago
I'm excited to see this feature coming to Redmine!
While testing our plugin, we found that permissions defined in the plugin weren’t loaded, blocking access to some features.
It seems that the change in r23837 — specifically, calling Redmine::AccessControl.public_permissions in config/initializers/30-redmine.rb before Redmine::PluginLoader.load is executed — is what causes the issue.
The Redmine::AccessControl.public_permissions method is implemented as follows:
def public_permissions
@public_permissions ||= @permissions.select {|p| p.public?}
end
If this method is called before plugin permissions are loaded into @permissions, the resulting @public_permissions will not include them, which causes the issue.
 Updated by Katsuya HIDAKA 8 months ago
Updated by Katsuya HIDAKA 8 months ago
I've attached a minimal patch that fixes the issue described in #note-44.
It ensures that Redmine::PluginLoader.load is executed before Doorkeeper.configure.
All tests have passed, as confirmed in the following:
https://github.com/hidakatsuya/redmine/actions/runs/15747468431
 Updated by Marius BĂLTEANU 8 months ago
Updated by Marius BĂLTEANU 8 months ago
The fix looks good to me.
Holger Just, Jens Krämer, can you take a look as well, please?
 Updated by Marius BĂLTEANU 6 months ago
Updated by Marius BĂLTEANU 6 months ago
- Related to Patch #43125: Remove redundant fixtures declaration from OauthProviderSystemTest added
 Updated by Go MAEDA 11 days ago
Updated by Go MAEDA 11 days ago
- Related to Patch #43713: Add missing entries "apps" and "shield-check" to icon_source.yml added